NAC Passby with Proxy
Platformed PC
- Add an USB network adapter to the Platformed PC
- Install FreeProxy (Administrator rights required)
- Create a SOCKS5 Proxy (Administrator rights required)
- Create a scheduled task to start FreeProxy on startup (Administrator rights required)
Raspberry Pi
- Assign static IP to the Raspberry Pi via /etc/network/interfaces
- Install DHCP server
- Configure the DHCP server (Required because plataformed PC's wont let you set an IP)
- Must assign static IP to the platformed PC
Physical Setup
- Connect the DCHP server (Raspberry Pi), the Platformed PC (Added USB adapter) and the PCs that will use the SOCKS5 proxy to a switch
- Setup OpenVPN to use a SOCKS5 Proxy (socks-proxy 192.168.0.11 1080)
Configuration Files
Raspberry Pi
sudo apt update
sudo apt upgrade
sudo apt install proxychains dnsutils isc-dhcp-server
/etc/network/interfaces
source-directory /etc/network/interfaces.d
auto eth0
iface eth0 inet static
address 192.168.0.1
netmask 255.255.255.0
gateaway 192.168.0.1
/etc/dhcp/dhcpd.conf
option domain-name "rra.lan";
option domain-name-servers 10.0.232.30, 8.8.8.8;
default-lease-time 60000000;
max-lease-time 720000000000;
ddns-update-style none;
authoritative;
log-facility local7;
subnet 192.168.0.0 netmask 255.255.255.0 {
range 192.168.0.1 192.168.0.200;
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.0.255;
}
host dhcpi {
hardware ethernet d8:eb:97:b9:5e:77;
fixed-address 192.168.0.1;
}
host WF0006D3 {
hardware ethernet D8:EB:97:B6:B7:6A;
fixed-address 192.168.0.11;
}
host WF0006D3Rafa {
hardware ethernet ec:8e:b5:77:3e:e1;
fixed-address 192.168.0.2;
}
/etc/default/isc-dhcp-server
INTERFACESv4="eth0"
INTERFACESv6=""
Enable & estart isc-dhcp-server service
sudo systemctl enable isc-dhcp-server
sudo systemctl restart isc-dhcp-server
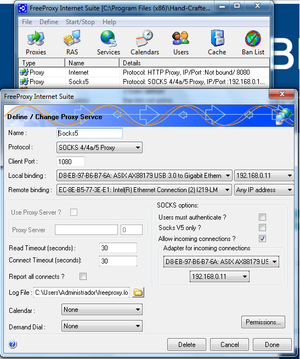
Platformed PC Free Proxy Configuration
Client PC openvpn file
dev tun
persist-tun
persist-key
cipher AES-256-CBC
ncp-ciphers AES-256-CBC
auth SHA512
tls-client
client
resolv-retry infinite
lport 0
socks-proxy 192.168.0.11 1080
remote 20.1.43.10 1194 tcp
verify-x509-name "pfSenseOperaciones.rra.lan" name
auth-user-pass
remote-cert-tls server
ca "/PATHTO/CA/FreeIPACA.crt"
tls-crypt "/PATHTO/keys/pfSenseOperaciones-tls.key" 1
cert "/PATHTO/certs/xeXXXXX.crt"
key "/PATHTO/keys/xeXXXXX.key"
auth-nocache
reneg-sec 0
verb 2
# auth-user-pass "/PATHTO/auth.txt" # Optional